As part of Team8’s ongoing cybersecurity research, we come up with a set of annual cybersecurity themes, together with our financial partner, WisdomTree.
These themes are meant to represent the key areas driving the future growth of cybersecurity each year. These themes also drive the WisdomTree-Team8 Cybersecurity Index, which is designed to track high-growth publicly-traded cybersecurity companies.
How Do We Do This?
We came up with the themes by engaging with experts and specialists across our Village (350+ C-level executives, many from Fortune 500 or Forbes Global 2000 organizations), the Team8 cybersecurity team, and our range of global advisors in order to highlight areas of immense future business growth and product development from a technology, market trends, regulatory, and venture funding standpoint.
We also considered Team8’s “Attacker Perspective” (our unique insights into how attackers think and operate), in addition to publicly-available information and research from a range of well-regarded sources. We then cross-referenced our findings with one-on-one interviews with CISOs & cyber defenders, confirming the top areas of acceleration in cybersecurity from the perspective of security leaders.
We considered both mature and nascent markets to gather a broad perspective and track early, emerging technologies that will influence the future and lead to high-growth opportunities in the next few years.
View the 2023 Themes and Notable Providers
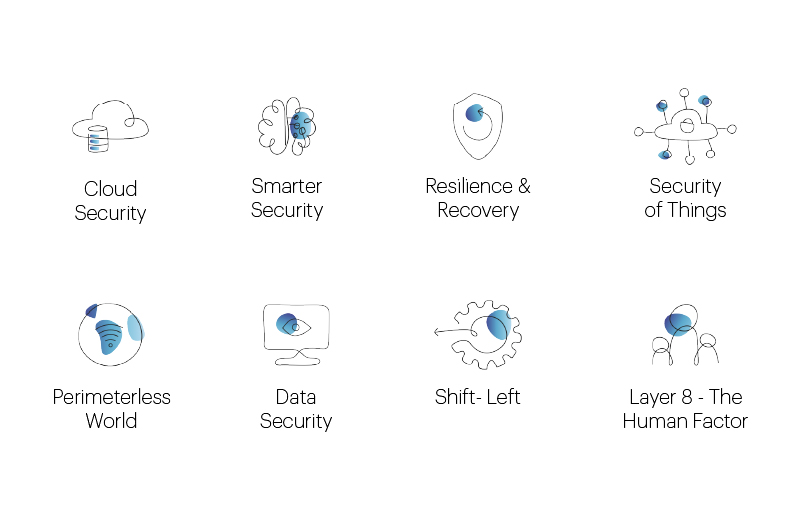
Introducing 2023 Cyber Themes:
The following represent Team8’s eight cybersecurity themes. Each theme includes the threats and technology trends driving it, as well as the impact of the theme and the key takeaways, as well as selected providers in each category.
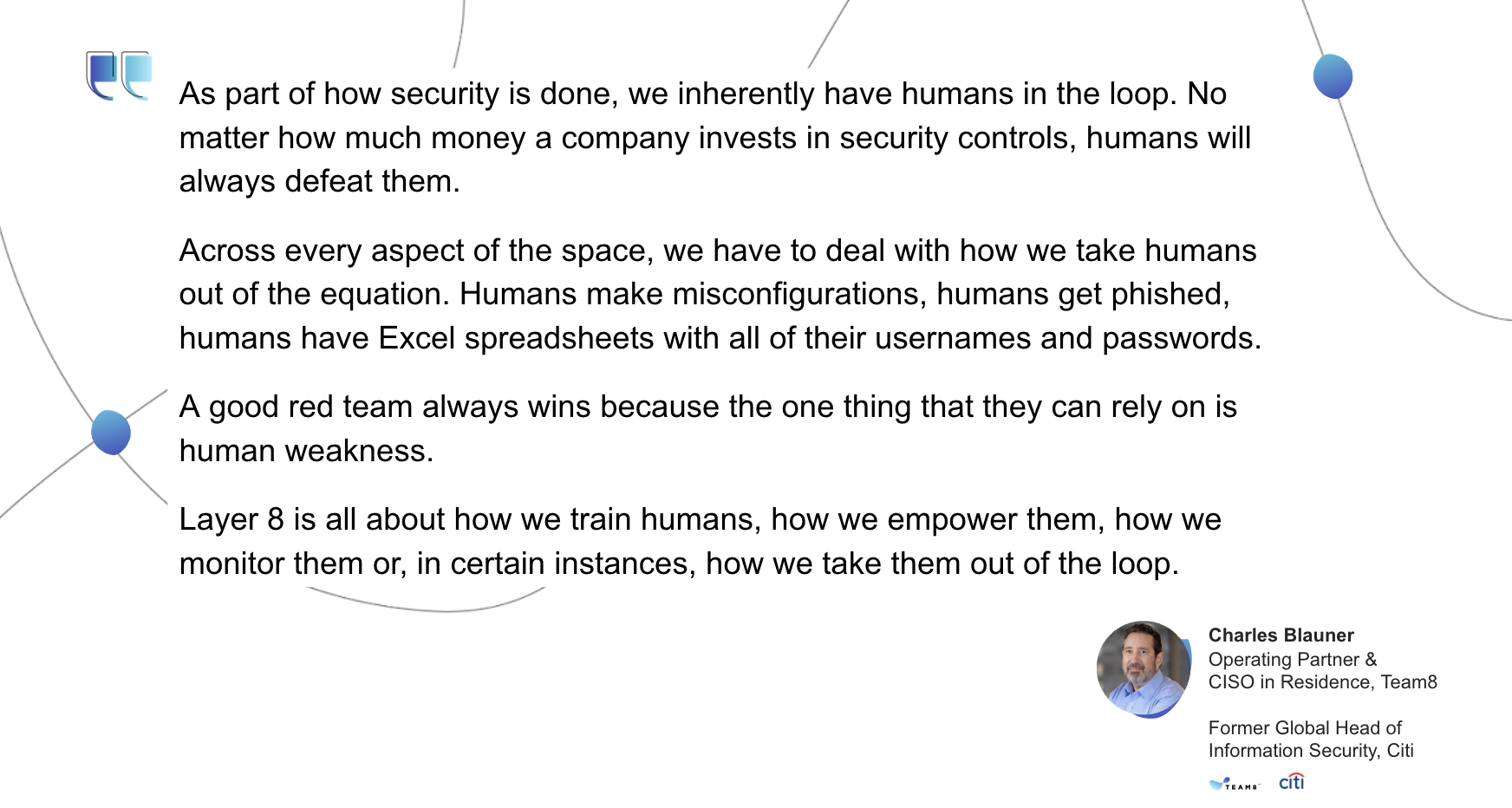
In 2023, for the first time an eighth theme was introduced, representing the human risk – Layer 8. For more information behind this theme in particular, see the announcement here.
- Cloud Security: Buoyed by tailwinds from the pandemic and digital transformation, cloud adoption is experiencing a meteoric rise, and enterprise cloud migrations are expanding from small, low-risk applications and experiments to business critical initiatives. As such, security capabilities are evolving to allow enterprises to reap the benefits of moving to the cloud, while retaining control over their security posture, data protection programs, and application integrity.
Impact:- Many companies, especially smaller ones, tend to use a single cloud plus SaaS strategy
- More sophisticated and/or mid-to-larger companies tend to think about multi-cloud for several reasons: for technical resilience, to prevent vendor lock-in, and for specialization of features.
- In order for cloud provider-based security solutions to be successful, the cloud providers themselves are going to have to be able to support their customers’ hybrid & multi-cloud environments.
- Resilience & recovery: In a world in which digital infrastructure is now business-critical infrastructure, cybersecurity cannot afford to stop at “identify, protect, detect, and respond”. Any sound security strategy must also consider resiliency and include the capability for rapid recovery from degradation, disruption, or denial of access to enterprise systems or data, and swift reconstitution of assets and capabilities.
Impact:- When thinking about resilience and recovery, cybersecurity must primarily focus on operational risk and resilience, i.e. the risk to business processes, including the underlying data and IT systems.
- Standard continuity of business processes are insufficient in the face of malicious cybersecurity action.
- Smarter Security: Cybersecurity is becoming highly complex and is becoming difficult and expensive to manage. At the same time, there is also a shortage of cybersecurity talent while, simultaneously, adversaries are increasingly leveraging sophisticated attack capabilities. All of this stretches response capabilities. Smarter security solutions will mitigate many of these challenges through the incorporation of automation, data, and AI to plug gaps and provide security teams with better options to best-use their human capital.
Impact:- Because of both the supply problem (lack of talent) and the demand problem (dramatic increase in volume/speed of attacks and AI-driven attacks), there may be no alternative other than automation and AI-supported defense.
- Security of Things: The growth of the Internet of Things (IoT) is driving digitization and unlocking business value. But Security of Things requires that every connected device or network – each with its own identifier and ability to transfer or process data – must be protected. Each of these devices acts as a potential breach-point into an organization or to private data, which increases overall risk exponentially.
Impact:- In the context of industrial IoT, there are concerns regarding the resiliency of critical infrastructure, and unfortunately, much of this infrastructure is decades old and difficult to secure.
- In general, there continues to be a massive acceleration in the number and variety of IoT devices, creating new categories of attack that need to be planned for in order to protect individuals, data, and enterprises.
- Perimeterless World: The enterprise perimeter is nearly obsolete, and the dramatic shift to remote work during the pandemic is accelerating its demise. This requires enhanced processes for identity and access management (IAM), with a growing use of zero trust architectures that provide better control.
Impact:- In the modern environment, there are many things outside of the network that still need to be trusted and depended upon.
- Thus, using network topology as the basis for trust simply isn’t a valid assumption any more, and that’s where identity comes into play.
- Data Security: On one hand, globalization and the growth of the digital economy are accelerating the need for digital collaboration. On the other, emerging privacy regulations and consumer preferences are driving investment in privacy-enhancing technologies and the means for users to have more control over their data. The net result of these colliding forces will be new data protection- and privacy-driven strategies that impact underlying architectural design and business processes. The need to mitigate data breaches is also driving more data security and privacy regulation.
Impact:- Data is at the heart of everything in the modern corporation, with concerns focused on confidentiality, data integrity, and data availability.
- While the focus has previously been on confidentiality, today there is an increased focus on availability. Integrity of data will be the last frontier for data security considerations.
- Shift-Left: Developing and managing software is more agile and faster than ever. However, developers currently have neither the expertise nor the tools to handle the security issues while the security team doesn’t have the staff to cover the gap. Cybersecurity needs to be shifted-left in the application development process to ensure that security considerations are embedded from the start.
Impact:- If Shift-Left works, the biggest impact will be that it enhances the relationship between security and AppDev, which will enable the faster creation of secure applications.
- However, in order for Shift-Left to work, security has to adapt to the way developers think, act, buy, and consume tools.
- Additionally, with the emerging focus on the “software bill of materials” (SBOM), the ability for software creators to track application componentry and provide evidence to their customers will be critical.
- Layer 8 – The Human Factor: No matter how much money a company invests in security controls, humans will always defeat them. A good red team always wins because the one thing that they can rely on is human weakness. Layer 8 is all about how we train humans, how we empower them, how we monitor them, or in certain instances, how we take them out of the loop.
Impact:- A common first entry point of an attacker to an organization is usually a human (employee), who can easily be compromised by malicious software, social engineering techniques, or simply by human error.
- Compromised employees allow attackers to bypass significant portions of companies’ defensive controls, and these humans cannot be “patched”.
- Thus, the human attack surface can only be mitigated by compensating controls.
View the 2023 Themes and Notable Providers
If you have feedback on the themes, and/or would like to discuss them further with us, please feel free to reach out at [email protected]
Team8 Disclaimer:
This 2023 Cyber Themes infographic represents the opinions of Team8 Labs Inc. (“Team8”) and is for informational purposes only. You should not treat any opinion expressed by Team8 as a specific inducement to make an investment in any security, but only as an expression of Team8’s opinions. Team8’s statements and opinions are subject to change without notice. Team8 is not registered as an investment adviser under the Investment Advisers Act of 1940, as amended (the “Advisers Act”), and relies upon the “publishers’ exclusion” from the definition of investment adviser under Section 202(a)(11) of the Advisers Act. As such, the information contained in this 2023 Cyber Themes infographic does not take into account any particular investment objectives, financial situation or needs and is not intended to be, and should not be construed in any manner whatsoever as, personalized investment advice. The information in this 2023 Cyber Themes infographic is provided for informational and discussion purposes only and is not intended to be, and shall not be regarded or construed as, a recommendation for a transaction or investment or financial, tax, investment or other advice of any kind by Team8. You should determine on your own whether you agree with the information contained in this 2023 Cyber Themes infographic. Certain of the securities referenced in this Team8’s 2023 Cyber Themes infographic may currently, or from time to time, be constituents of an index developed and maintained by WisdomTree Investments, Inc. using data provided by Team8, which has been or will be licensed for a fee to one or more investment funds. In addition, certain officers or employees of Team8 or funds or other persons or entities affiliated or associated with Team8 may hold shares of, be officers or directors of, or otherwise be associated with some or all of the issuers of the securities referenced in this 2023 Cyber Themes infographic or included in such index. Team8 expressly disclaims all liability with respect to any act or omission taken based on, and makes no warranty or representation regarding, any of the information included in this 2023 Cyber Themes