‘It’s tough to make predictions, especially about the future.’ — Yogi Berra
The evolution of the security market is driven by changes in the threat landscape; new threats create new security requirements. And with the COVID-19 pandemic, 2020 was quite a year for the threat landscape.
The pandemic accelerated the rate of digital transformation, driving faster uptake of cyber technologies and creating a larger threat surface and more opportunities for attackers. As the threat surface increased, so did security budgets with 57% of CISOs saying their security budgets increased this year, according to Team8’s 2021 CISO Survey.
Changes in the security market are also driven by innovation by security technology providers. At Team8, we try to stay on the leading edge of this innovation by looking at what trends will shape security in the future. With this in mind, we’re sharing the top seven areas we believe will be of critical importance to the cybersecurity industry in the next few years. We hope our list of trends will serve as a catalyst for deeper discussions in the industry on how to address some of the biggest challenges facing cybersecurity.
You can read more about these trends in our 2021 Cybersecurity Brief.
We identified these trends through conversations between our Team8 cybersecurity experts, many from Israel’s elite 8200 military intelligence unit, our global advisors, and our CISO Village — a community of 350+ C-level security executives from 300 enterprises, 25% of which are Fortune 500 and 55% of which are Forbes Global 2000. We also incorporated Team8’s “Attacker Perspective” (our unique insights into how attackers think and operate), our proprietary Team8 2021 CISO Survey and other Team8 internal resources, in addition to publicly-available information.
Our seven cybersecurity trends are:
#1 Cloud Security

2020 will go down as a pivotal year for cloud adoption as businesses sought to extend employee IT service access beyond the walls of the business, cut costs, retain flexibility, and throttle demand due to dislocation caused by the pandemic. In fact, Cloud Security (64%) is the number one investment area for 2021 according to the Team8 2021 CISO Survey, followed by Security Automation (53%) and Identity and Access Management (52%).
In retrospect, we expect that 2020 will be remembered not only as the year when cloud became the default, but also when the dynamics governing enterprise networks and workload deployments changed forever. In a world where containers offer the capability to combine hybrid, multi-cloud and on-premise compute and storage strategies, security tools and techniques will need to evolve to reduce complexity created by a multitude of new offerings within and beyond the enterprise perimeter. For example, workloads moving between different cloud environments to optimize for speed, scalability, cost, and compliance have created a new “shared responsibility” model between the enterprise and its different cloud providers. If not managed properly, this model can open the door for threat actors to identify and leverage misconfigurations as a way to gain access.
Impact: Cloud is becoming so complex it should be perceived as an operating system. Many of today’s “new” security solutions are just modern-day equivalents of endpoint security and other on-premise techniques which were never fully effective. Attacks are not only still happening, but are being amplified by the pervasiveness, speed, and connectedness of the cloud. Instead of applying legacy solutions to the cloud, organizations need security solutions that are architected for the cloud, combining control and integrity with scalability and agility.
#2 Security of Things

2020 saw a continuation of the explosion of connected devices, fueled by advancements in lower-power compute and communication, with IDC predicting there will be 55.7 billion connected devices worldwide by 2025. Entirely new types of devices are coming online, while old technologies that have been online for years under the radar, such as in manufacturing, remain vulnerable. 5G networking enables ubiquitous connectivity. As critical infrastructure and manufacturing sectors go online, spurred by advancements in smart machinery, IT and OT networks are converging.
Legacy systems are continuing to be connected to the Internet, as are Industrial IoT (IIoT) technologies like smart meters, automated asset distribution systems, and self-monitoring transformers, and production lines and farm equipment outfitted with sensors. Done right, IT-OT convergence unlocks tremendous business value — enabling improvements in operational efficiency, performance, and quality of service. But new threat types against new device types expose the need for better endpoint defese. Novel attack patterns and approaches are cropping up every day — ransomware, cryptojacking, new kinds of advanced persistent threats (APTs) — that require a shift from signature-based detection to more advanced and dynamic behavioral-based techniques. Enterprise security teams simply can’t stop them all and a lack of asset visibility and management, and security updates compounds the problem. Successful attacks go beyond data breaches — widespread disruption and harm, both physically and economically, is often the attacker’s endgame.
Impact: Although there has been an evolution in security for IoT devices and environments over the last few years, the shift in ransomware from focusing on data and IT infrastructure to disrupting OT environments is accelerating, and is now one of the greatest threats facing CISOs and CIOs today. Furthermore, as 5G proliferates, everything will become “a thing” and even in domains like OT, the concept of networks will dramatically change. IT security controls can’t adapt to work in OT environments. To mitigate risk of threats that cross the IT/OT boundary, new models and mindsets are needed.
#3 Perimeterless World
The traditional firewall approach assumed that enterprises could establish a strong perimeter, limit the number of access paths through the perimeter, and then intrinsically trust everyone and everything “inside’. Yet, even before the pandemic, cloud migration and the adoption of Software-as-a-Service (SaaS) applications were on the rise, causing perimeter-based controls to become increasingly hard to maintain, manage, and scale. Many enterprises also had existing Bring Your Own Device (BYOD) programs and robust mobile-first initiatives that perimeter-based controls were never designed to protect. Remote-first work will remain with us in a post-pandemic environment, with 72% of office workers indicating a desire to retain the flexibility to work remotely.
The global workforce has become reliant on at-home WiFi networks, non-hardened work devices, and online collaboration tools — all trends which have accelerated during 2020’s pandemic-enforced remote-work period. Without reliable connectivity, employees may not be getting the protection they need, and their non-hardened devices can also pose a significant risk to enterprise network security. A more porous perimeter with less oversight is also naturally more susceptible to insider threats, malicious or unintentional. Organizations must quickly move beyond perimeter-based solutions to secure the growing number of applications and resources hosted in the cloud, available as a service, and on mobile systems.
Impact: With more and more assets outside the walls of the enterprise, companies can no longer take a fortress approach to defend against threat actors. Employees, vendors, contractors, and customers are all connecting to the network from everywhere. Security strategies need to evolve to support new ways of doing business that drive growth, productivity, and competitive advantage.
#4 Privacy & Digital Trust
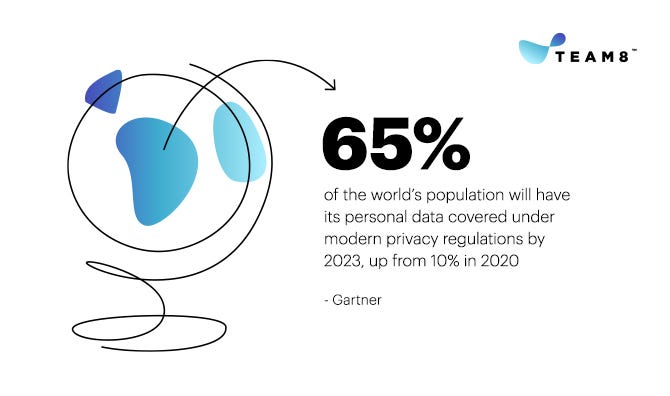
The recent history of high-profile data breaches is strengthening privacy regulations and eroding consumer trust in companies. Cisco’s 2020 Consumer Privacy Survey revealed that one-third of consumers are “Privacy Actives” who have stopped doing business with organizations over Data Privacy concerns. This trend is likely to continue as 65% of the world’s population will have its personal data covered under modern privacy regulations in the next two years, up from 10% in 2020.
Many organizations have a hard time keeping up with growing and ever-changing regulations because they lack an effective Governance Risk and Compliance (GRC) program, and because regulations often conflict with one another, making it costly and complicated to comply. To satisfy regulations and earn consumer confidence, organizations need to take a proactive approach with tools, systems, and services that help them get ahead of business risk by identifying and managing personal information within their enterprises and throughout the supply chain, respecting regional variations in data regulations, and transparently supporting consumers’ preferences and instructions about data sharing.
Impact: In the future, the use of personal data may be controlled by the individual to whom the data refers, which will drive changes in business models, regulations, and security. As consumers and companies become more proactive about imposing restrictions on the use and sharing of data, technologies that enable doing business without sharing data will take center stage and drive competitive advantage. Storing data that an enterprise doesn’t need has become a liability not worth assuming. Not knowing what data the enterprise has, and to whom it’s available, become unsustainable.
#5 Resilience & Recovery
Ransomware and destructive malware are on the rise, with Bitdefender finding that 2020 brought a seven-fold rise compared to the previous year. Opportunistic attackers are taking advantage of the surge in digitization and new security challenges during COVID-19 which, in combination, make organizations more vulnerable to cyber threats. Overall, the average severity of insurance claims reported by policyholders jumped by 65% from 2019 to 2020, driven largely by the rising costs of ransomware as cybercriminals ask for higher amounts of money and increasingly threaten to release stolen data publicly unless ransom is paid. An October 2020 United States Treasury directive, aimed at stymying ransom payments by threatening sanctions against enterprises who pay, could either provide a much needed headwind against this alarming trend, or leave enterprise leaders staring down the barrel of significant business disruption in the face of a severe ransomware attack, between a rock and a hard place.
As enterprises adjust to the business disruptions caused by the pandemic, disaster recovery and business continuity plans are critical. This isn’t only a matter of cybersecurity but also of operational resiliency. Any network outage or other disruption to infrastructure can put companies on the sidelines or entirely out of business for months. For many companies, there is no “Plan B” and in today’s climate that is a particularly dangerous position in which to be. Even the best security teams can succumb to advanced attacks, and knowing how to continue to offer services to customers during recovery from such attacks is essential.
Impact: Ransomware is just one example of the damage threat actors are causing businesses. Systems can be modified, data stolen, and infrastructure brought down for a variety of reasons. Companies need a reboot plan designed for the digital age, to build resiliency and accelerate recovery from damage or disruption.
#6 Shift-Left
Time-to-market is often prioritized over security. Developers are measured by how fast they can code, rather than on how securely. And business leaders are measured on how quickly they can provide new products and services to the market. With no time to fix insecure code at the source, security is often “bolted on” once an application is fully developed — a risky approach. As a result, 42% of organizations that experienced an external attack blame the incident on a software security flaw and 35% blamed a buggy web application. In today’s dynamic environment of micro-releases and daily or weekly software updates software developers need to maintain a security mindset and rely on controls throughout the coding process in order to get ahead of security issues.
Despite this, the migration to a developer-driven security paradigm has been slow; Google reports that only 20% of firms are considered “elite performers” with DevOps. “Shift-left” highlights the need for security teams to work with developers from the very beginning of the development lifecycle to build-in information security and security automation. Ideally, developers are empowered to embed security while creating a product or service, with tools that not only make code more secure, but also codify intent.
Impact: The farther left the shift, the more deeply security is integrated into the application development process. To achieve this, security professionals should hone their coding skills, and developers must have the tools, the training, and the incentives to code with security in mind.
#7 Smarter Security
Organizations are deploying and managing an increasing number of security tools to manage ever-expanding networks. In fact, larger organizations today deploy 130 cyber tools on average. CISOs are being bombarded by vendors with tools that solve specific problems but don’t interoperate. Beyond the initial purchase price, the hidden costs of managing these tools, making sense of the data generated and the time it takes for the security operations center (SOC) to tie all the tools and data all together to create actionable information are overwhelming. The global shortage of skilled cyber talent exacerbates the problem. By 2022, the global cybersecurity workforce shortage has been projected to reach upwards of 1.8 million unfilled positions.
Employers today are desperate for people with real technical skills who can design secure systems, create new tools for defense, and hunt down hidden vulnerabilities in software and networks. At a time when attackers are accelerating attacks by employing AI tools, the talent shortage leaves defenders farther and farther behind their adversaries. Smarter security can alleviate the deficit facing defenders by using automation not purely to eliminate human error or save money, but also to empower security teams to be able to defend against attacks at the same rate at which they’re happening.
Impact: Enterprises need software engineers and systems that are focused on APIs and more useful interfaces to enhance security analyst productivity. They need tools that facilitate comprehensive security orchestration. And they need smarter security that leverages automation, data, and AI so that humans can focus on decision making around exceptions, while security solutions analyze data, automate processes, learn over time, and automatically enforce policies.
Final Thoughts
Cybersecurity is going through a historic shift as companies accelerate their digital transformation, systems become more complex and expansive, and attacks become more sophisticated and frequent. We are entering a new age for the industry as it grows and matures, and what happens now will help set the stage for the next cybersecurity cycle and the corresponding generation of companies it yields.
Click here to download our 2021 Cybersecurity Brief, outlining these seven trends and more.
Originally appeared on Medium





