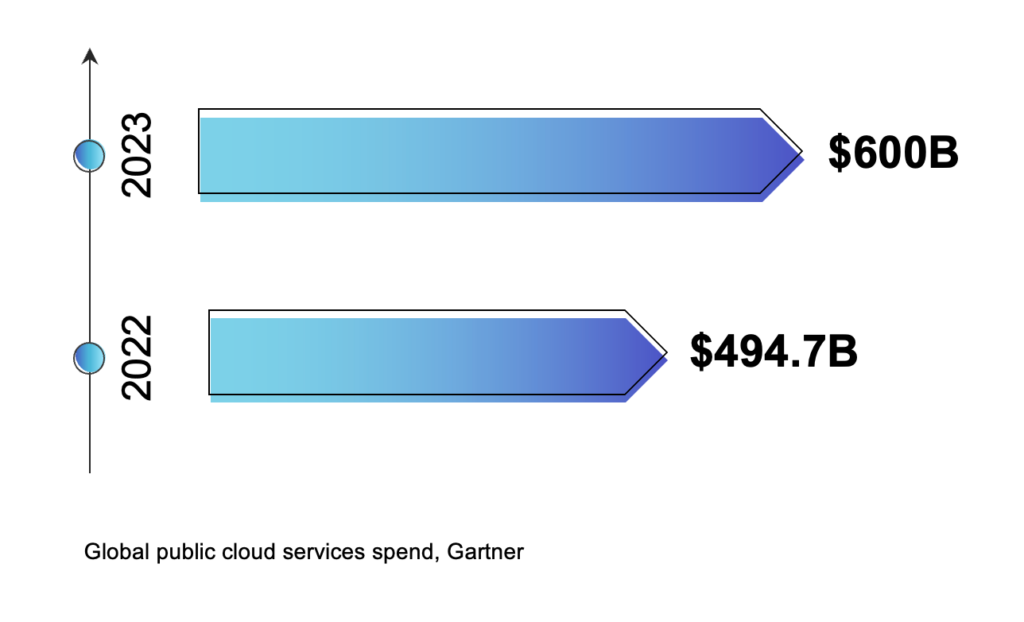
Cloud adoption continues to rise at an accelerated pace. According to Gartner, global public cloud services spend is expected to grow by 20.4% this year (2022) to $494.7 billion and approach $600 billion in 2023. However, cloud migration and adoption might lead to implementing technology without the necessary cloud security considerations.
Cloud implementations come with additional complexities compared to those of standard on-premises environments. For example, advanced permission models (owned by different teams) and rapid cloud-native development often introduce new risks into enterprise cloud environments.
Poor cybersecurity hygiene also contributes to successful attacks against various startups, enterprises, and government agencies operating in the cloud. According to the Analysis Report (AR21-013A by the Cybersecurity & Infrastructure Security Agency (CISA), social engineering tactics like phishing and failure to adhere to cloud security best practices have helped threat actors successfully attack various organizations.
To tackle global cybersecurity challenges, organizations must strategize and use multiple tools and expertise to respond to the current threat level.
Poor Cloud Security Practices Often Cause Data Breaches
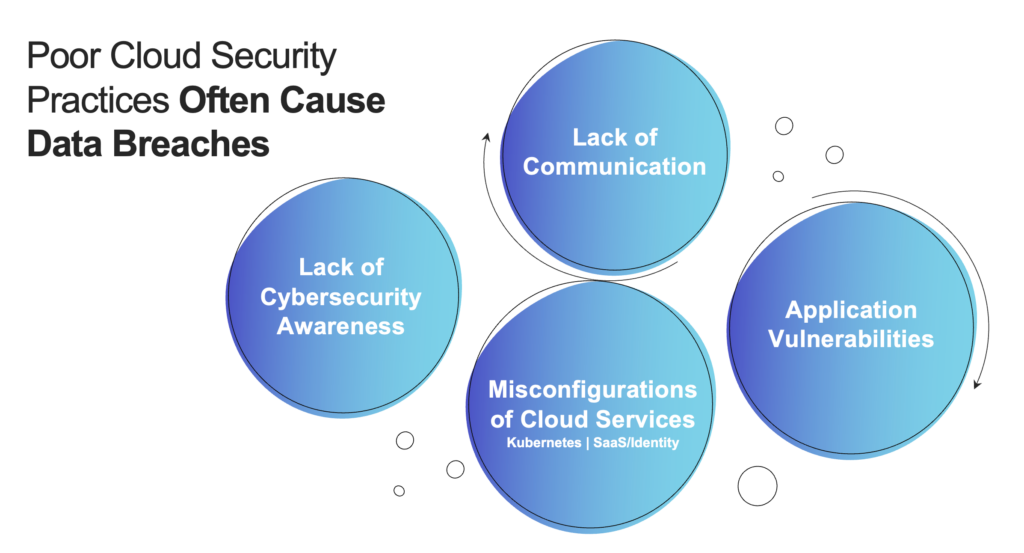
When we at Team8 look at the cause of most cloud breaches, we see a few types of attacks, originating from human error, cloud misconfigurations, known vulnerabilities, sophisticated tactics, or a combination of some of the above.
Security events are often caused by one or more of the following.
Lack of Communication
Cloud security risks grow exponentially when developers adopt new tools independent of the security team. Adding new cloud-native technologies into enterprise cloud infrastructure without the involvement of security teams has the potential to create vulnerabilities.
Lack of Cybersecurity Awareness
Sometimes, it can also be as simple as staff getting tricked into sharing their credentials in a social engineering campaign (including multi-factor authentication fatigue). For example, the Yanluowang ransomware group recently breached Cisco’s corporate network by using an employee’s stolen credentials after hijacking their personal Google account (with user credentials synched from the browser).
An additional example is the recent Uber breach by a social engineering attack on one of its employees. Here, the attacker managed to gain lateral movement inside the organization due to exposed secrets and credentials within Uber’s own network.
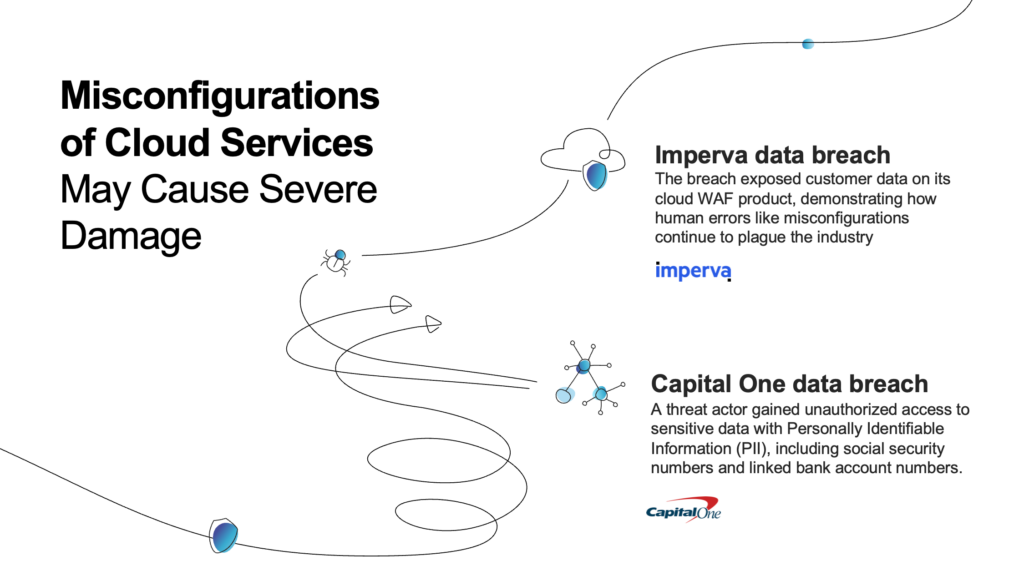
Misconfigurations of Cloud Services
Cloud complexities often lead to misconfigurations. For example, a misconfiguration of cloud services was the primary culprit behind the Capital One data breach. In this case, a threat actor gained unauthorized access to sensitive data with Personally Identifiable Information (PII), including social security numbers and linked bank account numbers.
And from the Imperva data breach that exposed customer data on its cloud WAF product, we also see that human errors like misconfigurations continue to plague the industry.
Misconfigurations of Kubernetes
Kubernetes is highly customizable, but various configuration options can affect an enterprise’s cloud security posture. Any Kubernetes misconfiguration may lead to unwanted disclosures, which threat actors can use to escape and escalate privileges.
Furthermore, user interfaces, APIs, and CLI commands can be highly attractive to hackers. Although a misconfiguration doesn’t always lead to exposed instances and the loss of sensitive data, a simple misconfiguration can make an organization a lucrative target.
Automating Kubernetes processes as much as possible helps alleviate some misconfiguration issues. By leveraging security tools instead of humans, security teams can provide guardrails that allow DevOps teams to configure Kubernetes and containers more securely.
Misconfigurations of SaaS/Identity
Organizations have benefited from the convenience provided by software-as-a-service (SaaS) applications. However, SaaS applications and identity platforms come with security risks. This is because SaaS platforms have complex configurations and permission settings that can cause problems during cloud migration.
SaaS misconfigurations have provided significant cause for concern, with CISA even publishing a report (AR19-133A) on recommended best practices to mitigate this risk (especially during cloud migrations).
Application Vulnerabilities
Attacks can also start by exploiting vulnerabilities inside the applications deployed in the cloud environment. This can open a pathway for an attacker to reach inside the organization’s cloud environment and expand from there.
Finding a vulnerability inside a proprietary application might be difficult. However, in most cases, developers build applications on top of existing open-source libraries, and hackers may try to use a known vulnerability that the organization hasn’t yet patched.
This issue is often caused by not updating the application dependencies or not maintaining a proper SBOM, or a wider and more dynamic list of software components.
Robust Cloud Security Demands a Multipronged Approach
Secure cloud infrastructure requires much more than security tools. Although many cloud security tools can help security teams mitigate risk, they are simply not enough to prevent or respond to cyberattacks effectively.
Security tools tend to fall short because you have to know how to use them—and how to use them together—without introducing new vulnerabilities. This can be challenging due to the ongoing cloud security skills shortage.
As such, to fortify cloud infrastructure, enterprises must take a multipronged approach to cloud security by adopting some of the following cybersecurity frameworks.
Cybersecurity Mesh Architecture
Cybersecurity Mesh Architecture (CSMA) helps extend security controls in a composable and scalable manner across widely distributed assets. As it’s flexible in nature, CSMA is highly suitable for hybrid multi-cloud architectures.
For example, CSMA encourages coordination between different security tools and interoperability. Instead of using siloed security tools, the cybersecurity mesh enables solutions to work together through the use of support layers, including consolidated policy management, identity fabric, and security intelligence.
This approach negates the need to protect all digital assets with one security tool. Instead, organizations can secure individual endpoints in a more dynamic environment and eliminate the use of obsolete standalone systems.
CSMA improves the company’s defense posture through collaboration between different tools and makes security more agile and scalable on demand.
Cyber Defense Matrix
Cyber Defense Matrix, written by security expert Sounil Yu, aims to help enterprises identify security gaps and the tools to address them effectively. For example, the framework presented—of the same name—clearly shows how security teams can use the following together and in an effective manner:
- Cloud security posture management (CSPM)
- Cloud workload protection platform (CWPP)
- Security orchestration, automation, and response (SOAR)
- Cloud-native detection and response (CNDR)
- Incident response (IR)
CWPP and CSPM can be integrated, centralized, and unified to properly secure cloud-native applications across the entire application lifecycle (CNAPP – cloud-native application protection platforms).
The primary objective is to use the Cyber Defense Matrix to gain complete visibility at a glance into the execution of your cloud security strategy and prioritize investments accordingly. This approach essentially brings organization and order to the complex cybersecurity landscape.
With the benefit of a comprehensive view of all assets and security measures, including those of third-party providers, cloud security engineers can quickly recognize gaps in current security controls and rapidly respond to active security events.
The DIE Model
The distributed immutable ephemeral (DIE) security model was created by Sounil Yu. It focuses on creating an infrastructure that is as distributed, immutable, and ephemeral as possible in order to enable a better security posture of the hybrid infrastructure controlling the data.
The traditional CIA model focuses on evaluating your security based on confidentiality, integrity, and availability. DIE, on the other hand, focuses on aspects of your system that directly advance security. DIE is crucial to minimizing complexity and enforces a security-by-design approach instead of a bunch of security tools.
Strong Authentication and Identity Access Controls
Strong authentication and identity access controls play a critical role in digitally transformed organizations. Modern-enterprise cybersecurity strategies must include tools like identity access management (IAM) and multi-factor authentication (MFA) to verify user identity and authorize controlled access to company devices and resources across your enterprise infrastructure.
Having robust identity and access control helps ensure that the right people have seamless access across applications to complete their work at the right time. These solutions optimize a company’s security capabilities and prevent threat actors and unauthorized users from gaining access to and moving laterally across enterprise networks.
Organizations should also complement authentication and access management controls with granular policy controls for data protection, as well as implement conditional access (CA) policies. For example, you can establish and apply granular access controls to prevent someone from copying and pasting, taking a screenshot, sharing files with external third parties, downloading data to local storage, or printing a file with sensitive data.
Organizations will be better prepared to respond to advanced threats when they use some of these different cybersecurity frameworks and tools effectively together. As the threat level and technologies evolve, a multipronged approach to cloud security will also be easier to manage at scale.
We at Team8 know that current tools alone are insufficient and that enterprises today require a different approach—one more suitable for cloud infrastructure to better understand how to protect a cloud environment and act upon CISA recommendations. Currently, this is one of our research and ideation directions at Team8, which aims to protect the cloud and eliminate cloud threats and risks.
Download the infographics / executive summary here